ClamAV, the open-source antivirus engine, isn’t just some dusty old program; it’s a constantly evolving beast battling the ever-changing landscape of malware. From its humble beginnings, ClamAV has become a critical component in many systems, silently protecting users and servers from digital threats. This deep dive explores its history, architecture, and the ongoing fight against malicious code.
We’ll cover everything from its core scanning algorithms and integration with other systems to optimizing its performance and understanding its limitations. Think of this as your comprehensive guide to mastering ClamAV, whether you’re a seasoned sysadmin or just starting your cybersecurity journey. Get ready to geek out!
ClamAV History and Evolution
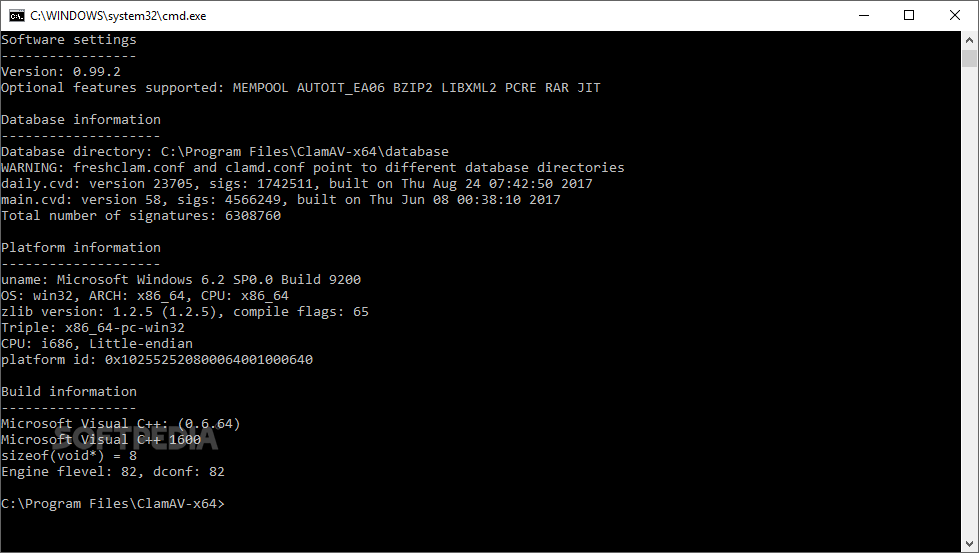
ClamAV, a venerable open-source antivirus engine, boasts a rich history marked by continuous development and significant performance enhancements. Its journey reflects the ever-evolving landscape of malware and the constant arms race between security software and malicious actors. Understanding this evolution provides insight into its current capabilities and future potential.
ClamAV’s development began in 1993, initially as a simple signature-based scanner. Over the years, it has transformed into a sophisticated system incorporating various detection methods, making it a powerful and widely used tool for protecting systems from various threats.
ClamAV Release Timeline and Feature Additions
Tracking ClamAV’s major releases highlights the iterative improvements in its functionality and performance. While a complete list is extensive, focusing on key milestones provides a clear picture of its progress.
| Version | Release Date (Approximate) | Significant Features |
|---|---|---|
| 0.10 | 1993 | Initial release, basic signature-based scanning. |
| 0.90 | 2001 | Improved signature database management and detection capabilities. |
| 0.97 | 2005 | Introduction of on-access scanning capabilities. |
| 0.99 | 2008 | Significant performance optimizations and enhanced multi-threading. |
| 0.100 | 2010 | Improved database updates and support for more file types. |
| 0.101 | 2012 | Enhanced heuristic analysis and improved detection of polymorphic malware. |
| 0.102 | 2015 | Further performance enhancements and improved handling of large files. |
| Current Versions (e.g., 0.103+) | Ongoing | Continuous updates with improved detection rates, new signature types, and performance optimizations. |
Evolution of ClamAV’s Scanning Engine and Core Algorithms
ClamAV’s scanning engine has undergone a substantial evolution, moving beyond simple signature matching to incorporate more advanced techniques. This evolution has been crucial in addressing the increasing sophistication of malware.
Initially relying solely on signature-based detection, ClamAV now incorporates heuristic analysis, which examines file behavior and characteristics to identify potentially malicious code even without a known signature. This layered approach significantly enhances its detection capabilities. Furthermore, advancements in its core algorithms have led to more efficient pattern matching and improved speed, enabling faster scanning of larger datasets.
Performance Improvements Across ClamAV Versions
Performance improvements have been a consistent focus throughout ClamAV’s development. These improvements are multifaceted, encompassing faster scanning speeds, reduced resource consumption, and enhanced scalability. While precise quantitative data requires specific benchmark testing and depends heavily on hardware and the size/type of scanned data, anecdotal evidence and user reports consistently point to significant performance gains across major versions.
For example, comparing early versions (pre-0.99) to more recent versions (0.102 and beyond) reveals substantially faster scan times, particularly for large datasets. This is largely due to improved algorithms, optimized code, and the utilization of multi-core processors. The reduction in resource consumption, such as memory usage and CPU load, has also been significant, making ClamAV more suitable for resource-constrained environments.
ClamAV Architecture and Components
ClamAV’s architecture is designed for efficiency and scalability in detecting malware. It’s a modular system, allowing for flexibility and extensibility, making it adaptable to evolving threat landscapes. Key components work together seamlessly to provide comprehensive virus scanning capabilities. Understanding these components is crucial for effective deployment and management of ClamAV.ClamAV’s core functionality revolves around several key components working in concert.
These components handle different aspects of the virus detection process, from database updates to actual file scanning and reporting. The efficient interaction between these components is vital for the software’s performance and accuracy.
Freshclam: Database Updates
The `freshclam` utility is essential for maintaining ClamAV’s effectiveness. It’s responsible for regularly downloading and updating the virus signature database from the ClamAV servers. This database contains the signatures – essentially, the patterns – that ClamAV uses to identify known malware. Without regular updates from `freshclam`, ClamAV would become increasingly ineffective against new and emerging threats. The frequency of updates is configurable, allowing administrators to balance the need for up-to-date protection with potential network bandwidth constraints.
A typical update process involves downloading a compressed database file, verifying its integrity, and then replacing the existing local database. This ensures that ClamAV always has the latest information on known malware variants.
Data Flow in ClamAV Scanning
The following table illustrates the data flow during a ClamAV scan:
| Stage | Component | Input | Output |
|---|---|---|---|
| 1. File Submission | ClamAV Scanner (e.g., `clamscan`) | File path or file data | File data (passed to the next stage) |
| 2. Signature Matching | ClamAV Engine | File data | Match or no match indication, along with details (if a match is found) |
| 3. Result Reporting | ClamAV Scanner | Match/no match indication and details | Scan report (to the user or another system) |
| 4. Action (Optional) | External System (if configured) | Scan report | Quarantine, deletion, or other actions based on the scan result |
This simplified diagram shows a typical scanning process. The actual flow might be more complex depending on the specific ClamAV configuration and the use case (e.g., real-time scanning vs. on-demand scanning). The key takeaway is the sequential processing of the file, from initial submission to the generation of a scan report, possibly followed by actions based on the results.
Virus Detection Methods Used by ClamAV
ClamAV employs a multi-layered approach to virus detection, combining signature-based and heuristic methods to identify both known and unknown malware. This dual approach aims to maximize detection rates while minimizing false positives, although a perfect balance remains a challenge in the ever-evolving landscape of cyber threats. Understanding these methods is crucial to appreciating ClamAV’s effectiveness and limitations.
Signature-based detection and heuristic analysis represent two fundamental strategies in antivirus technology. Signature-based detection relies on identifying known malware through matching specific patterns (signatures) within a file. Heuristic analysis, on the other hand, employs behavioral analysis and pattern recognition to identify potentially malicious code even without pre-existing signatures. ClamAV utilizes both methods synergistically to enhance its detection capabilities.
Signature-Based Detection in ClamAV
Signature-based detection is the cornerstone of many antivirus engines, including ClamAV. It works by comparing the input file against a vast database of known malware signatures. These signatures are essentially unique code snippets or characteristics that identify specific viruses or malware families. When a match is found, ClamAV flags the file as infected. The effectiveness of this method hinges on the comprehensiveness and timeliness of the signature database.
Regular updates are essential to keep up with the constantly emerging threats. The process is relatively fast and resource-efficient for known threats.
Heuristic Analysis in ClamAV
Heuristic analysis is crucial for detecting zero-day exploits and new malware variants that lack established signatures. ClamAV’s heuristic engine examines file behavior, code structure, and other characteristics to identify potentially malicious patterns. This involves analyzing code for suspicious functions, unusual file structures, or attempts to modify system settings. For example, a heuristic engine might flag a file that tries to execute code from a temporary directory or attempts to self-replicate.
While effective against novel threats, heuristic analysis is more computationally intensive and carries a higher risk of false positives.
Comparison of Signature-Based and Heuristic Detection
Signature-based detection offers high accuracy and speed for known malware. However, it is ineffective against zero-day threats or polymorphic viruses that constantly change their code to evade signature detection. Heuristic analysis, while slower and prone to false positives, provides a crucial layer of defense against unknown malware. The combination of both methods allows ClamAV to achieve a better balance between detection rates and accuracy.
Limitations and False Positives
A major limitation of signature-based detection is its reliance on updated signatures. A delay in updating the signature database can leave the system vulnerable to known threats. Heuristic analysis, conversely, is susceptible to false positives, where benign files are incorrectly flagged as malicious due to their behavior or code structure resembling that of malware. For example, a program using complex encryption might be mistakenly flagged as malicious.
Sophisticated heuristic engines attempt to minimize false positives through various techniques, but a certain level of uncertainty remains inherent in the process. ClamAV continuously strives to improve the accuracy of both its signature-based and heuristic engines to balance detection capabilities and minimize false positives.
ClamAV’s Integration with Other Systems
ClamAV’s power truly shines when integrated into existing IT infrastructure. Seamlessly embedding it into your email, web, and file-sharing systems provides a robust, proactive defense against malware. This section details the common methods for integrating ClamAV into these critical areas.
ClamAV Integration with Email Servers
Integrating ClamAV with email servers like Postfix and Sendmail is crucial for preventing malicious emails from reaching your users. This involves configuring the mail server to scan incoming and outgoing emails using ClamAV before delivery or sending. This prevents the spread of viruses and other malware via email. For Postfix, this typically involves using the `milter` (Mail Filter) interface, which allows external programs like ClamAV to intercept and scan emails.
Sendmail offers similar functionality, often through custom configuration and the use of its `milter` framework. Specific configuration details vary depending on the mail server and operating system, but generally involve specifying the path to the ClamAV scanner and setting appropriate parameters for scanning attachments and email body content.
ClamAV Integration with Web Servers
Protecting web servers from malicious uploads and files requires integrating ClamAV into the server’s file handling processes. With Apache, this often involves using modules like `mod_security` or custom scripts to trigger ClamAV scans before files are uploaded or served. Nginx offers similar functionality through custom modules or external scripts that interface with the ClamAV daemon. A common approach is to configure the web server to scan uploaded files before they are stored, preventing the spread of malware through website uploads.
This integration might involve using a custom script that’s triggered on file upload events, initiating a ClamAV scan and only allowing the file to be stored if the scan comes back clean.
ClamAV Integration with File Sharing Systems
Integrating ClamAV into file sharing systems, like those based on NFS or Samba, adds a layer of security to shared resources. This often involves configuring the file sharing system to trigger ClamAV scans whenever files are accessed, modified, or uploaded. This approach can be implemented using hooks or scripts that are triggered by file system events, providing real-time protection against the spread of malware through shared files.
For example, a script could be configured to run a ClamAV scan whenever a new file is added to a shared directory. The script would then take appropriate action based on the scan results, such as quarantining or deleting infected files. The specific implementation depends heavily on the file sharing system and its scripting capabilities.
ClamAV Performance Optimization
So, you’ve got ClamAV up and running, but it’s feeling a little sluggish? Don’t worry, optimizing ClamAV’s performance is totally doable. There are several strategies you can employ to significantly boost scanning speed and reduce resource consumption, leading to a smoother, more efficient antivirus experience. This involves understanding how ClamAV works under the hood and making strategic adjustments to its configuration.Optimizing ClamAV performance hinges on effectively managing its resource usage and leveraging its capabilities.
Factors like the size of your database, the number of files being scanned, and the hardware resources available all play a significant role. By strategically adjusting ClamAV’s settings and utilizing advanced features like multi-threading, you can dramatically improve its efficiency.
Multi-threading and Parallel Processing
Multi-threading and parallel processing are game-changers for ClamAV’s speed. Instead of scanning files one by one, ClamAV can divide the workload among multiple threads, significantly reducing overall scan time. This is particularly beneficial when dealing with large numbers of files or very large files. The impact is directly proportional to the number of CPU cores available; more cores mean more threads can run concurrently, resulting in faster scans.
Imagine scanning a terabyte of data – with single-threaded scanning, this could take hours; with multi-threading on a powerful machine, the scan time can be reduced to a fraction of that. The practical effect is a noticeable improvement in response time and a decrease in the strain on system resources.
Best Practices for ClamAV Configuration
Proper configuration is key to unlocking ClamAV’s full performance potential. Here’s a rundown of best practices to get you started:
- Update your virus definitions regularly: Fresh signatures are crucial for accurate and efficient detection. Outdated definitions can lead to slower scans and missed threats.
- Use a fast and reliable database server: The speed at which ClamAV accesses its virus definition database directly impacts scan times. A fast local drive or a networked server with low latency is essential.
- Optimize database location and access: Place the ClamAV database on a fast storage device (SSD preferred) to minimize I/O bottlenecks. Avoid network shares unless absolutely necessary, as network latency can significantly slow down scans.
- Adjust the number of threads: Experiment with different thread counts to find the optimal balance between speed and resource usage. The ideal number will depend on your system’s CPU core count and available RAM.
- Utilize ClamAV’s built-in optimization features: ClamAV offers various command-line options and configuration settings that can be fine-tuned for optimal performance. Consult the ClamAV documentation for details on these features.
- Consider using a caching mechanism: Caching previously scanned files can dramatically reduce scan times, especially for frequently accessed files or directories. ClamAV doesn’t have built-in caching, but external tools or scripts can be used to implement this.
- Regularly check and clean your database: Over time, the virus definition database can become fragmented and bloated, negatively impacting performance. Regularly purging old or unnecessary database entries can help maintain optimal speed.
ClamAV’s False Positive and Negative Rates
Okay, so we’ve talked about how ClamAV works, but no system is perfect. Even the best antivirus software will occasionally misidentify files, leading to false positives (flagging harmless files as malicious) or false negatives (missing actual threats). Understanding these inaccuracies is crucial for effectively using ClamAV.False positives and false negatives in ClamAV stem from a complex interplay of factors.
The core issue lies in the inherent difficulty of definitively identifying malicious code. Malware authors constantly evolve their techniques, creating new variations that can evade detection. Furthermore, the sheer volume of files scanned daily makes it nearly impossible to guarantee 100% accuracy. Another contributing factor is the use of heuristics – educated guesses based on patterns – which, while helpful, can sometimes lead to misidentification.
Finally, the signature database itself, while regularly updated, might lag behind the emergence of the newest threats.
Okay, so ClamAV’s pretty solid for virus scanning, right? But if you’re talking about full system backups, that’s a totally different ballgame. For that, you’d probably want something like norton ghost , which is awesome for imaging your whole drive. Then, after you’ve got your backup, you can totally relax knowing ClamAV will keep your system clean from malware.
Factors Contributing to False Positives
Several factors can lead to ClamAV flagging benign files as malicious. These include overly broad signature definitions that might match legitimate code segments, heuristic analysis mistaking benign code for malicious behavior, and even simple coding similarities between harmless applications and known malware. For instance, a program legitimately using a particular code sequence might trigger a false positive if that sequence is also present in a known virus.
This highlights the challenge of balancing sensitivity (detecting as many threats as possible) with specificity (avoiding false positives).
Factors Contributing to False Negatives
Conversely, false negatives occur when ClamAV fails to detect actual malware. This can be due to several reasons: newly emerging malware that hasn’t yet been added to the signature database (zero-day exploits), sophisticated malware designed to evade detection through techniques like polymorphism or code obfuscation, and limitations in the heuristic analysis engine. For example, a newly created virus with unique code might slip through the cracks until its signature is added to the database.
Similarly, a virus that dynamically modifies its code to avoid detection could easily evade traditional signature-based scanning.
Minimizing False Positives
Reducing false positives involves a multi-pronged approach. Regularly updating the ClamAV virus definitions is paramount; this ensures that the latest signatures are available to accurately identify known threats. Additionally, carefully examining the ClamAV logs for patterns of false positives can help identify overly broad or inaccurate signatures that need adjustment. Finally, tuning the ClamAV configuration to be less sensitive, potentially at the cost of slightly reduced detection rates, can minimize the occurrence of false positives in specific contexts.
For example, disabling heuristic scanning or adjusting the scanning depth might be considered in situations where false positives are excessively disruptive.
Improving ClamAV’s Accuracy
Improving the accuracy of ClamAV is an ongoing process. Keeping the virus database up-to-date is essential, as it’s the primary weapon against known malware. Implementing more sophisticated heuristic analysis algorithms that can better differentiate between benign and malicious code is another key area. Regular testing and feedback mechanisms, where users can report false positives and negatives, are vital for continuous improvement and refining the detection engine.
Finally, exploring and integrating newer detection techniques, such as machine learning and behavioral analysis, could significantly enhance ClamAV’s overall accuracy.
ClamAV’s Command-Line Interface (CLI)
ClamAV’s command-line interface (CLI) provides a powerful and flexible way to interact with the antivirus engine. It allows for granular control over scanning processes, offering options not readily available through graphical interfaces. This direct interaction is crucial for scripting, automation, and advanced troubleshooting.ClamAV’s CLI uses the `clamscan` command, which offers a wide array of options to customize scans.
These options allow you to specify target files, directories, email messages, and control the level of detail in the output. Understanding these options is key to effectively using ClamAV for virus detection.
File and Directory Scanning
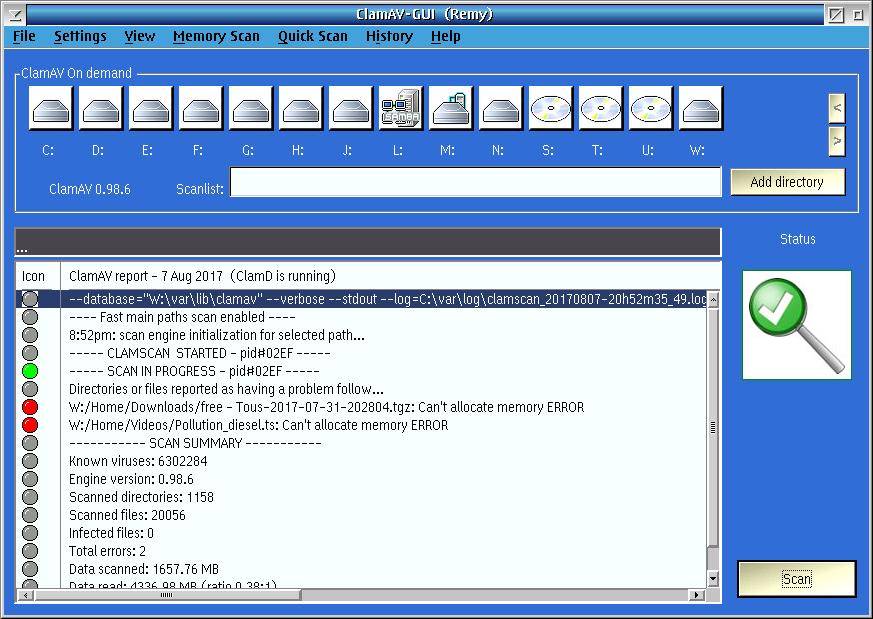
The most basic use of `clamscan` involves specifying the file or directory to scan. For a single file, you simply provide the file path as an argument. For example, `clamscan my_document.pdf` will scan `my_document.pdf`. To scan a directory, use the `-r` (recursive) option: `clamscan -r /path/to/directory`. The `-i` option will only display infected files, while `-l` will output the results to a log file.
Combining these options allows for targeted and efficient scanning. For instance, `clamscan -r -i -l scan_results.log /home/user/Downloads` will recursively scan the Downloads directory, only displaying infected files and logging the results to `scan_results.log`.
Email Message Scanning
Scanning email messages requires slightly different handling. ClamAV can scan various email formats, including .eml files. Similar to file scanning, you provide the file path. For example, `clamscan suspicious_email.eml` will scan the email. However, for larger mailboxes or mail servers, more sophisticated methods are generally preferred, often involving integration with mail transfer agents (MTAs) or dedicated email security solutions.
This integration typically happens outside the direct `clamscan` command.
Performing a Full System Scan
A full system scan with ClamAV’s CLI involves recursively scanning crucial system directories. This is not a simple one-line command, as it requires careful consideration of which directories to include and exclude to avoid unnecessary delays and potential conflicts. The following steps Artikel a safe and effective approach:
- Identify Target Directories: Determine which directories to scan. This usually includes `/home` (user directories), `/tmp` (temporary files), and potentially other directories containing frequently downloaded files. Avoid scanning directories like `/proc`, `/sys`, and `/dev`, as these contain system-level files that are not relevant for virus scanning and attempting to scan them could cause errors or delays.
- Create a Scan Script (Optional but Recommended): For a full system scan, a shell script is recommended. This allows for better organization and control. The script should include the `clamscan` command with appropriate options, such as `-r` (recursive), `-i` (infected files only), and `-l` (log file). Error handling and logging mechanisms should be included within the script.
- Execute the Scan: Run the script with appropriate privileges (likely as root or using `sudo`). The scan will take a considerable amount of time depending on the size of the system and the speed of the hardware. Regularly monitor the log file for progress and any errors.
- Review the Log File: After the scan completes, thoroughly examine the log file for any detected viruses. Take appropriate action based on the findings.
Example Shell Script (Illustrative – Adapt to your system):
#!/bin/bash
clamscan -r -i -l /var/log/clamscan.log /home /tmp
echo "Scan complete. Check /var/log/clamscan.log for results."
Remember to always back up your data before performing a full system scan, as a false positive could lead to the deletion of important files (though ClamAV’s false positive rate is generally low). Additionally, ensure you have sufficient disk space and system resources available for the scan.
ClamAV’s Database Management
ClamAV’s effectiveness hinges on its constantly updated virus definition database. This database, a crucial component of the system, contains signatures – essentially patterns – that ClamAV uses to identify malicious code. Understanding its structure, update process, and management strategies is key to maintaining a secure and efficient antivirus system.The ClamAV virus definition database is structured as a collection of files, organized logically to facilitate efficient searching and updating.
These files contain the virus signatures, which are essentially patterns or characteristics that identify malicious software. The database is not a single monolithic file, but rather a structured collection of data, often compressed to minimize storage space. The organization allows ClamAV to quickly search relevant sections of the database rather than scanning the entire thing for each file.
This significantly improves performance.
Database Update Process Using freshclam, Clamav
The `freshclam` utility is the heart of ClamAV’s database update mechanism. It periodically connects to the ClamAV servers to download and install the latest virus definitions. This process involves downloading updated signature files and integrating them into the existing database. The frequency of updates is configurable, allowing for flexibility based on security needs and network bandwidth. A typical update cycle might involve downloading several compressed files containing new or updated signatures, then verifying their integrity before replacing or merging them into the existing database.
This ensures that the antivirus system is always equipped to handle the latest threats. Successful updates usually result in a log message indicating the version of the database and the number of new signatures added. Failure to update can leave your system vulnerable.
Managing Database Size and Storage
The ClamAV database can grow quite large over time, consuming significant disk space. Several strategies can be employed to manage its size and storage. Regularly deleting old or unnecessary database versions can free up considerable space. Additionally, implementing a robust update schedule, rather than allowing the database to grow unchecked, helps to control its size. Using a compressed database format further reduces the storage footprint.
Network bandwidth limitations might also influence update frequency, requiring careful consideration of when to download updates and how frequently to run `freshclam`. In environments with limited storage or bandwidth, optimizing the update process is critical. For instance, scheduling updates during off-peak hours can minimize impact on network performance.
Security Considerations with ClamAV
ClamAV, while a powerful antivirus tool, isn’t immune to security risks. Its effectiveness and the security of the systems it protects depend heavily on proper installation, configuration, and ongoing maintenance. Ignoring security best practices can leave systems vulnerable to exploitation, potentially allowing attackers to bypass ClamAV’s defenses or even leverage ClamAV itself for malicious purposes.Potential security vulnerabilities in ClamAV installations stem from various sources, including outdated software, insecure configurations, and vulnerabilities in the underlying operating system.
These weaknesses can be exploited by malicious actors to gain unauthorized access to systems, install malware, or perform other harmful actions. This section will explore these vulnerabilities and Artikel mitigation strategies.
Vulnerabilities Associated with ClamAV
Several factors contribute to potential ClamAV vulnerabilities. One key concern is the use of outdated ClamAV versions. Older versions often contain known security flaws that have been patched in later releases. Failure to update ClamAV regularly exposes systems to attacks that exploit these known vulnerabilities. Another risk factor is improper configuration.
Incorrectly configured ClamAV settings, such as overly permissive access controls, can inadvertently weaken the system’s security posture. Furthermore, vulnerabilities within the underlying operating system on which ClamAV is installed can indirectly compromise ClamAV’s effectiveness. A compromised OS could provide attackers with a foothold to bypass ClamAV’s defenses. Finally, weaknesses in the ClamAV database itself, such as the inclusion of malicious signatures, could lead to false negatives or even compromise the system.
Securing ClamAV Installations and Configurations
Robust security practices are crucial for protecting ClamAV installations. Regular updates are paramount; automatically updating ClamAV to the latest version ensures that known vulnerabilities are patched promptly. This can often be achieved through the package manager of the underlying operating system or by using the ClamAV update mechanisms directly. Implementing strong access controls is equally important.
Restricting access to ClamAV’s configuration files and databases to authorized users only prevents unauthorized modifications or tampering. Furthermore, running ClamAV with appropriate privileges (least privilege principle) limits the potential damage that could be caused if a vulnerability is exploited. Regular security audits should be performed to assess the security posture of the ClamAV installation and identify any potential weaknesses.
This includes checking for outdated packages, misconfigurations, and potential vulnerabilities in the system’s overall security.
Preventing Exploitation of ClamAV Vulnerabilities
Preventing malicious actors from exploiting ClamAV vulnerabilities requires a multi-layered approach. Employing a robust intrusion detection and prevention system (IDS/IPS) provides an additional layer of defense, capable of detecting and blocking suspicious activity targeting ClamAV or the systems it protects. Regularly scanning the system for malware, using both ClamAV and other security tools, helps to identify and remove any malicious software that might have already gained access.
Network segmentation can limit the impact of a successful attack by isolating the ClamAV server from other critical systems. Sandboxing potentially dangerous files before scanning them with ClamAV minimizes the risk of executing malicious code. Finally, monitoring ClamAV’s logs for suspicious activity can help to identify potential compromises or attacks in their early stages. For example, an unusually high number of failed login attempts or unexpected changes to ClamAV’s configuration files could indicate a security breach.
ClamAV’s Role in a Multi-layered Security Approach
ClamAV, while a powerful tool, isn’t a standalone solution for comprehensive security. Think of it as a crucial component within a larger, multi-layered defense system. Its primary function is to detect and prevent malware from entering your network or infecting your systems, but it needs to work in concert with other security measures for optimal protection. A robust security strategy employs multiple layers to address various attack vectors and vulnerabilities.ClamAV excels at identifying known malware signatures, acting as a first line of defense against common threats.
However, it’s less effective against zero-day exploits or sophisticated attacks that utilize polymorphic or metamorphic techniques. This is where the importance of a layered approach becomes clear; ClamAV’s limitations are addressed by integrating it with other security tools like firewalls, intrusion detection/prevention systems (IDS/IPS), and data loss prevention (DLP) solutions. By combining these technologies, a more comprehensive and resilient security posture is achieved.
ClamAV Compared to Other Antivirus Solutions
Several antivirus solutions exist, each with its strengths and weaknesses. Choosing the right solution depends on factors like budget, system resources, and specific security needs. Some solutions focus on real-time protection and proactive threat hunting, while others prioritize signature-based detection, similar to ClamAV. Others may specialize in endpoint protection, network security, or cloud-based security.
Comparison of Antivirus Technologies
| Antivirus Technology | Strengths | Weaknesses | Typical Use Cases |
|---|---|---|---|
| ClamAV | Open-source, lightweight, command-line interface, suitable for servers and embedded systems, good for signature-based detection. | Limited real-time protection, less effective against zero-day exploits and polymorphic malware, requires manual updates. | Email servers, file servers, web servers, embedded systems, network security scanning. |
| Sophisticated Commercial Antivirus (e.g., McAfee, Symantec) | Real-time protection, heuristic analysis, behavioral monitoring, automatic updates, robust support. | Can be resource-intensive, expensive, potentially intrusive. | Desktops, laptops, mobile devices, enterprise networks. |
| Endpoint Detection and Response (EDR) Solutions (e.g., CrowdStrike, Carbon Black) | Advanced threat detection, behavioral analysis, incident response capabilities, threat hunting. | Complex to implement and manage, requires specialized expertise, can be expensive. | Enterprise networks, critical infrastructure protection. |
| Sandboxing Solutions (e.g., Cuckoo Sandbox) | Dynamic malware analysis, identification of unknown threats, detailed analysis reports. | Resource-intensive, can be slow, requires specialized expertise. | Malware research, advanced threat analysis, incident response. |
Future Trends and Developments in ClamAV
ClamAV, while a robust and widely-used antivirus engine, faces an ever-evolving landscape of malware threats. To maintain its effectiveness, continuous development and adaptation are crucial. Future trends will likely focus on improving detection accuracy, enhancing performance, and adapting to the increasingly sophisticated tactics employed by cybercriminals.The future of ClamAV hinges on several key areas for improvement and expansion.
These enhancements will ensure its continued relevance in the fight against malware, even as attack vectors become more complex and diverse.
Improved Machine Learning Integration
Machine learning (ML) is already playing a role in antivirus solutions, and its integration into ClamAV will likely deepen. Future versions could leverage more advanced ML algorithms for more accurate malware identification and reduced false positives. For example, a shift towards deep learning models could allow ClamAV to better analyze file structures and behaviors, identifying subtle patterns indicative of malicious activity that traditional signature-based methods might miss.
This improved accuracy would translate to a more effective and reliable antivirus experience for users.
Enhanced Performance and Scalability
As the volume of data processed by antivirus engines continues to grow, performance optimization is paramount. Future developments in ClamAV might include optimized database structures, improved multi-threading capabilities, and the incorporation of hardware acceleration techniques. For instance, utilizing GPUs to accelerate signature matching or ML model inference could significantly speed up scanning processes, allowing ClamAV to handle larger datasets and protect more systems efficiently.
This increased scalability is essential for dealing with the growing number of devices and the increasing size of files.
Advanced Threat Detection Techniques
The rise of polymorphic and metamorphic malware necessitates more sophisticated detection methods. Future ClamAV versions might incorporate techniques like behavioral analysis, sandboxing, and emulation to detect malicious activities even without relying solely on signature matching. Behavioral analysis, for example, would monitor the actions of a program in a controlled environment, flagging suspicious behavior regardless of its code signature.
This proactive approach would greatly improve the ability to detect zero-day exploits and other novel malware variants.
Improved Integration with Cloud Services
Cloud-based threat intelligence is becoming increasingly important. Future ClamAV implementations might incorporate tighter integration with cloud-based services to leverage real-time threat data and updates. This would allow for quicker responses to emerging threats, enabling ClamAV to identify and neutralize new malware strains much faster than relying solely on locally stored databases. This dynamic approach would provide a significant advantage in the ever-changing threat landscape.
Enhanced API and Integration Capabilities
Improved APIs and more streamlined integration with other security tools will be essential. This will allow easier integration into broader security ecosystems, allowing ClamAV to work seamlessly with firewalls, intrusion detection systems, and other security software. A well-defined and easily accessible API would make ClamAV a more versatile and valuable component of comprehensive security solutions. For example, a more robust API would enable developers to build custom tools and integrations for specific use cases, maximizing ClamAV’s utility.
Conclusive Thoughts
So, there you have it – a whirlwind tour through the world of ClamAV. From its humble beginnings to its current role as a vital security tool, ClamAV continues to adapt and evolve in the face of ever-more sophisticated threats. Understanding its strengths, weaknesses, and optimal configurations is crucial for anyone serious about cybersecurity. Whether you’re bolstering your home network or securing a large-scale server infrastructure, ClamAV deserves a place in your arsenal.
Now go forth and fight the good fight against malware!
General Inquiries: Clamav
What’s the difference between ClamAV and other antivirus solutions like McAfee or Norton?
ClamAV is open-source and command-line driven, making it highly customizable and adaptable. Commercial solutions often offer more user-friendly interfaces and potentially more advanced features, but they come with a price tag. ClamAV is a great choice for those who prioritize flexibility and cost-effectiveness.
How often should I update my ClamAV virus definitions?
As often as possible! Ideally, configure `freshclam` to run daily. Malware evolves rapidly, so keeping your definitions up-to-date is crucial for effective protection.
Can ClamAV scan encrypted files?
No, ClamAV cannot directly scan the contents of encrypted files. To scan them, you’ll need to decrypt them first.
What should I do if ClamAV flags a false positive?
Carefully review the flagged file. If you’re confident it’s benign, you can add it to ClamAV’s exception list. You can also report the false positive to the ClamAV developers to help improve their detection accuracy.